Cyber security compliance: the key to building trust with our customers

In today's digital landscape, where cyber threats loom large and data breaches dominate headlines (think Optus and Medibank), effective cyber security compliance is no longer optional – it's essential.
For technology companies like Felix, entrusted with safeguarding the sensitive data our customers share, this responsibility is paramount. That's why we've built a robust cyber security compliance program, and in this blog post, I'll delve into how it safeguards customer data.
Overview of the Felix cyber security compliance program
At Felix, our Cyber Security Compliance program has developed a set of policies, procedures, and controls across all aspects of the business to protect against cyber threats.
Our policies, procedures, and controls are specifically designed to conform to ISO 27001, SOC 2, and the EU's GDPR to provide peace of mind for our customers across the world. The combination of these frameworks formed the core of Felix's Cyber Security "prime directives" to ensure our platform's confidentiality, integrity and availability in managing our cyber security risks.


Benefits of knowing your provider's cyber security compliance
An effective cyber security compliance program can provide several benefits to our customers:
- Enhanced data protection: Our rigorous security measures act as a multi-layered shield against hacking, malware, and denial-of-service attacks, minimising the risk of data breaches and putting your mind at ease.
- Minimised financial and regulatory risks: Robust compliance helps you avoid costly data breaches and potential regulatory fines, safeguarding your bottom line and reputation.
- Built-in supply chain protection: We recognise the interconnected nature of your operations. By extending our security measures to vendors within your supply chain, we create a holistic protective ecosystem.
The ever-evolving cyber security threat landscape
The cyber security threat landscape is constantly evolving and becoming more sophisticated. According to the Australian Signals Directorate (ASD), both state and non-state actors continue to show the intent and capability to compromise networks (ASD 2023).
The numbers paint a stark picture:
- In FY22-23, the ASD received nearly 94,000 cybercrime reports, an increase of 23% from the previous financial year.
- On average, a cybercrime is reported every 6 minutes in Australia.
- The average self-reported cost of cybercrime to business had also increased by 14% each year for two consecutive years.
The professional, scientific and technical services sector reported the highest ransomware-related cyber security incidents.
Additionally, the ASD reported that over 92.6% of the cybercrime incidents were from small businesses with annual turnovers below $2 million. These small businesses commonly form a portion of our customers' supply chain and interact on the Felix platform as vendors.
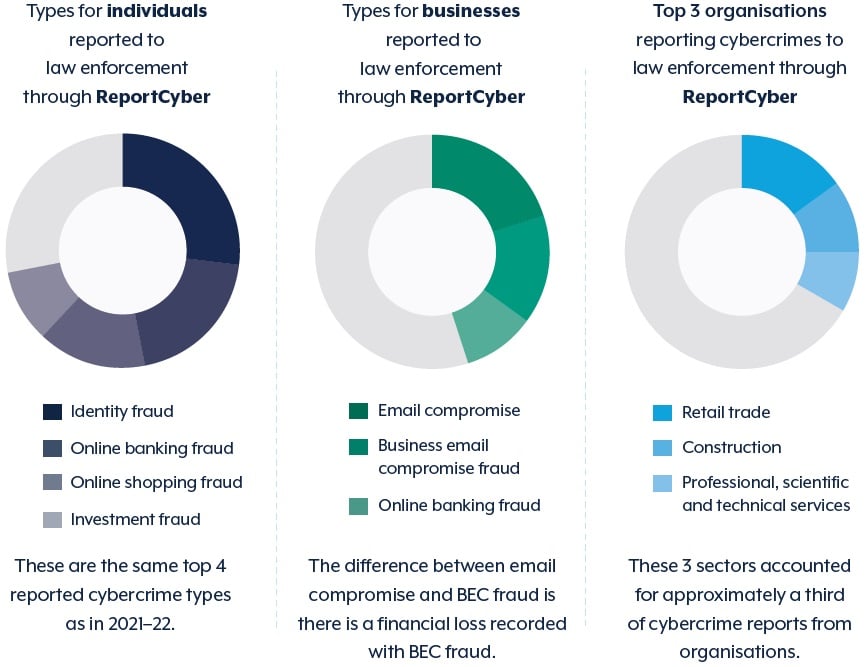 Cybercrime types. Source: cyber.gov.au
Cybercrime types. Source: cyber.gov.au
Security controls and preventive measures
Felix has implemented a wide range of security measures to keep customer data safe, including:
- Advanced encryption: Data at rest and in transit is shielded with robust encryption algorithms.
- Granular access controls: Only authorised personnel can access sensitive information, ensuring multi-layered protection.
- 24/7 automated SIEM monitoring: Our vigilant systems constantly scan for anomalies and potential threats, preventing breaches before they can occur.
- Regular audits and pen testing: We regularly subject our systems to external audits and penetration testing to identify and address any vulnerabilities.
- System availability: Our cloud-based infrastructure scales automatically and offers seamless failover to a secure data centre in another Australian city, or even within the Indo-Pacific region, in case of extreme disasters.
We have also recently fortified our defences, collaborating with leading security partners to strengthen our Security Information and Event Management (SIEM) capabilities. This advanced system identifies and addresses potential threats before they disrupt business operations.
Furthermore, recognising the increased vulnerability of small businesses in our customers' supply chains, Felix has been hard at work to bolster several security features offered to our vendor users.
Since October, we've proactively equipped select vendor users with an extra layer of defence against account takeover attempts. With Okta's multi-factor authentication and dynamic geo-location blocking in place, vendors are significantly less vulnerable if compromised by email phishing attacks.
We will be rolling these enhancements out progressively to all vendor users in the coming months, and we strongly encourage everyone to enable these features as soon as they become available, maximising their protection and contributing to a stronger overall security ecosystem.
Conclusion
At Felix, we see cyber security compliance as more than just a box to tick; it's the cornerstone of our commitment to protecting customer data.
Our processes, procedures, and controls, validated and audited against ISO 27001, SOC 2, and GDPR standards, demonstrate this dedication. We take data security seriously, no matter where our customer or their supply chain operate.
Felix's vigilance never sleeps. We keep a pulse on the evolving cyber landscape, staying ahead of the latest threats and trends. This commitment, not just to meet industry standards but to surpass them, is what truly builds trust.

Recent Articles
Supplier Relationship Management: Top 10 Do's and Don'ts.
Supplier relationship management (SRM) is the backbone of a resilient supply chain. When procurement teams manage suppliers effectively, they reduce risk, improve performance, and streamline delivery across large project environments. Whether you are modernising your vendor management system or replacing manual spreadsheets, these essential do's and don'ts will help you strengthen your SRM strategy.
2025 in review: Milestones, insights and achievements
2025 – a year of that brought meaningful developments for Felix as we continue to address the evolving needs of organisations navigating complex supply-chain environments.
Top 10 reasons for a centralised vendor database
As organisations grow, so does the complexity of managing vendor relationships. Many still rely on spreadsheets or siloed systems, which can lead to inefficiencies, data inconsistencies, and compliance risks. A centralised vendor database offers a smarter, more scalable solution that brings structure, visibility, and control to procurement operations.
Here are the top 10 reasons why centralising your vendor data is a strategic move.
Let's stay in touch
Get the monthly dose of supply chain, procurement and technology insights with the Felix newsletter.





