When an unexpectedly high demand lands on a system unprepared to handle the situation, we would have a similar story to how the MyGov and Centrelink online portal crashed last week.
Nearly 100,000 Australians sought welfare help via the government website, only to find it unavailable. More than 120,000 tried the following day and faced the same issue.
Whether it was a cybersecurity breach, or purely a system overload, the moral of the story is clear. In the age of remote working amid COVID-19, we turn to technology to ensure business continuity. But have we given technology the attention it deserves to see us through this crisis?
As the next instalment of our Business Continuity Planning series, we’ll uncover some common IT pressure points, as well as ways to mitigate these risks.
Is your IT infrastructure equipped for remote working?
Many organisations who already implemented a work-from-home policy before the crisis might not experience a huge learning curve.
For others, who either deal with a large workforce, or are less advanced in their digitisation journeys, this could put an enormous stress on their IT systems.
As we’ve seen with the MyGov story, any major announcement can change the situation for businesses overnight. Issues might arise if you find your remote workforce increase by more than 5 times in a short timeframe.
|
Issue |
Consequence |
|
Not enough work devices |
Possible downtime due to equipment purchase/set-up lead time |
|
Inadequate videoconferencing, collaboration tools |
Each department picks its own software, resulting in security vulnerabilities, or decreased productivity due to inconsistencies |
|
Poor internet connection in employees’ homes |
Reduced productivity |
|
Inadequate connection to company’s networks |
Reduced productivity, possible downtime while waiting for upgrade/maintenance of on-premise system |
Is your organisation’s culture fit for remote working?
As mentioned in our previous blog of the series, companies are being “forced into the world’s largest work-from-home experiment.” For many that had not even allowed remote working before Covid-19, this would be a formidable change management task.
Policies and processes alone might not be enough, even though they need to be established. If it is as much about a new way of life (social distancing) as it is a new way of working, we need to incorporate more behaviour-changing techniques. For instance:
- Rapid training for tools adoption
- Leaders becoming role models
- Reviewing performance evaluation process
- Providing regular company-wide updates
Not sure where to start to safeguard your IT systems and data? Download this handy checklist.“Getting a tool adopted requires twice the investment of having it developed in the first place.”
How robust are your cybersecurity measures?
In the latest survey by the Business Continuity Institute, only 53.3% of Australian organisations have reviewed cybersecurity arrangements to ensure systems remain secure in case of mass staff absences (compared to 64.9% globally).
Tumultuous times trigger fear and uncertainty, which could be exploited by bad actors. For instance, a recent global cyber-attack took advantage of people wanting to know more about the spread of COVID-19 by embedding malware behind “Coronavirus maps.”
More time spent online coupled with prolonged self-isolation periods may also lead to irrational actions, e.g. clicking on suspicious links.
What does this all mean in the business context? If remote workers use company laptops that have not been properly configured for protection, and there are no contingency plans, an organisation might be exposed to a dangerous “infection” much like coronavirus itself.
Practice cyber-hygiene and a healthy dose of scepticism:
- Are those emails containing an invoice or order acknowledgement phishing scams?
- Are those verification request emails leading to login pages of systems that hold sensitive data (e.g. personal email, financial accounts)?
- Is someone claiming to provide financial help or health information related to COVID-19 via email?
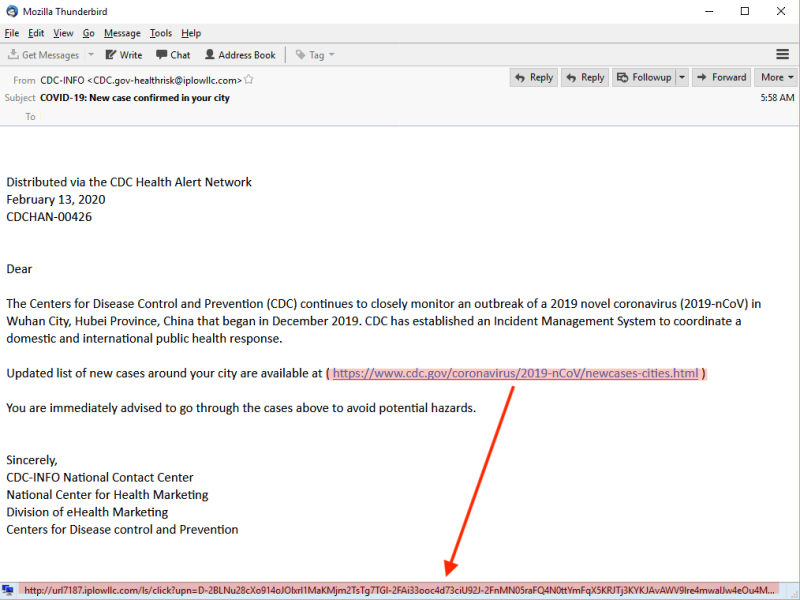
Example of phishing using a malicious link
Are your key systems available to ensure business continuity?
For organisations with paper-based or manual procurement processes that heavily rely on spreadsheets, email, and even physical presence, operational procurement might stall.
As companies look to quickly secure supply and onboard vendors, the onus is on the procurement/supply chain function to make it work. And they need technology to work as well.
There is nothing more frustrating than a technical glitch or unavailable service (cue the MyGov story) disrupting a critical operation.
Assess your technology stack to mitigate any degradation of service:
- ERP
- Procurement: including supplier relationship management, sourcing, P2P
- Accounting and payroll
Not only that, there should also be succession plans for key personnel too, so that organisations don’t get locked out of their own systems if these people suddenly cannot continue working.
Keep an eye on the future
It is tempting to pull resources, halt projects and cut whatever costs possible during this pandemic. However, organisations might be incurring invisible future expenses, especially if the affected initiatives were designed to increase efficiency or open up new revenue streams in the first place.
For instance, a digital transformation program for procurement could be underway pre-coronavirus. Instead of accelerating the migration to cloud-based systems, one might choose to temporarily revert to the old way (e.g. spreadsheets) until things get better.
While it’s still too early to measure concrete “savings” from the program suspension, the company may soon find themselves fighting the same fire they had hoped to avoid – only with the added pressure from Covid-19.
Hence, it’s important to re-evaluate priorities, shift resources, and track progress.
“Companies that take a slash-and-hold approach fare worse than those that both prune and thoughtfully invest.”
Conclusion
As we go through long periods of social distancing, people rely heavily on technology to stay connected and keep businesses going.
But sometimes technology fails us, for various reasons that could be traced back to the pre-coronavirus era.
The imperative now is to work swiftly with what we have, adapt, and invest for the future. Stay tuned for the next instalment of our series, where we will discuss measures to protect supply chain & operations in the short and long run.
---
You may be interested in our past webinar on risk mitigation with Bank of Queensland's former Chief Risk Officer. Check it out here.

Recent Articles
Supplier Relationship Management: Top 10 Do's and Don'ts.
Supplier relationship management (SRM) is the backbone of a resilient supply chain. When procurement teams manage suppliers effectively, they reduce risk, improve performance, and streamline delivery across large project environments. Whether you are modernising your vendor management system or replacing manual spreadsheets, these essential do's and don'ts will help you strengthen your SRM strategy.
2025 in review: Milestones, insights and achievements
2025 – a year of that brought meaningful developments for Felix as we continue to address the evolving needs of organisations navigating complex supply-chain environments.
Top 10 reasons for a centralised vendor database
As organisations grow, so does the complexity of managing vendor relationships. Many still rely on spreadsheets or siloed systems, which can lead to inefficiencies, data inconsistencies, and compliance risks. A centralised vendor database offers a smarter, more scalable solution that brings structure, visibility, and control to procurement operations.
Here are the top 10 reasons why centralising your vendor data is a strategic move.
Let's stay in touch
Get the monthly dose of supply chain, procurement and technology insights with the Felix newsletter.






